Monitoring for Okta breaches using BetterCloud Workflows

[ad_1]
November 7, 2023
Days ago, Okta announced they had been hacked after several weeks of customers and researchers reporting issues with the service. Thankfully Okta has since remedied the problem, and offered a series of steps customers can take to detect any unusual behavior in their Okta environment which may indicate a security breach of Okta services. While these recommendations should put their customers at ease, they add to an already overwhelming amount of work for IT teams.
Fortunately, like many other things, BetterCloud can automate these tasks away. In this post, we’re going to walk you through how to use our no-code workflow builder to set up workflows to monitor Okta behavior and proactively detect if you’ve been compromised.
Background
In this most recent Okta security breach, an adversary utilized a stolen credential to access Okta’s support case management system. Once inside Okta’s system, the hacker accessed files uploaded by Okta customers using valid session tokens from recent support cases where customers uploaded HTTP Archive (HAR) files for troubleshooting. Regrettably, this allowed the threat actor to gain complete access to many of Okta’s customers’ systems.
Monitoring is crucial going forward
Given this breach shares many similarities with other recent breaches, it’s essential for Okta customers to proactively monitor and secure their Okta environment. Okta’s official recommendations post-breach unfortunately put more work on customers, including asking customers to strip session tokens from files they share with the Okta support team. IT teams should assume these session tokens will be shared, as would be normal in any enterprise support setting.
Until additional security measures are implemented, the next best thing would be for IT to proactively monitor Okta usage inside of their business to get early indications of an Okta breach. Cloudflare, 1Password, and BeyondTrust were all able to do this using advanced monitoring techniques. With BetterCloud, you can as well.
Automate security and monitoring with BetterCloud
IT teams should deploy the following workflows to secure and then monitor their Okta environment.
Require MFA for all users
Mandating multifactor Authentication for all users is a good practice, and a good first step customers can take towards preventing hackers from using stolen Okta credentials against themselves. Provided users are enrolled in a group that has a MFA requirement as part of onboarding, BetterCloud makes this a task IT can do quickly.
Simply filter the User 360 grid by application type, select all of its users, and use the Add to Group action to enroll these users in MFA.
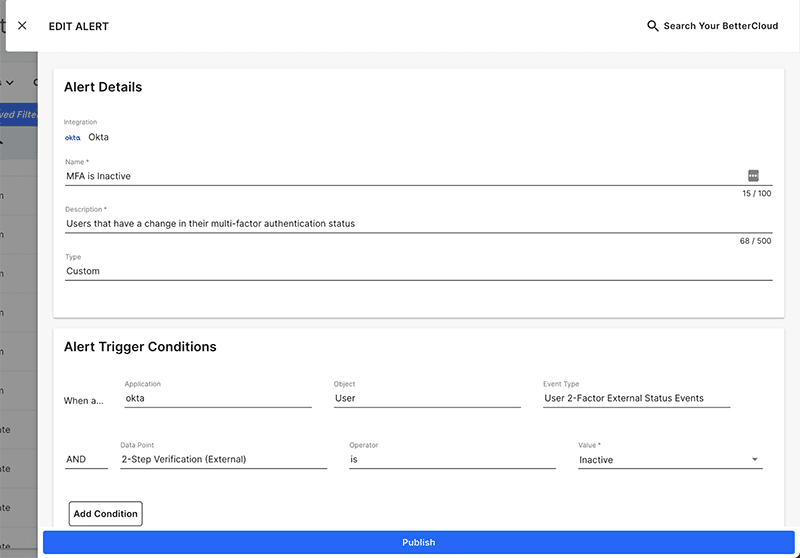
Alert for Okta MFA disabled
Another behavior common in these Okta breaches is for adversaries to disable MFA on Okta users in order to more easily gain access to Okta customer systems. BetterCloud can alert IT teams when an Okta user doesn’t have MFA enabled any longer, allowing IT to investigate and take action.
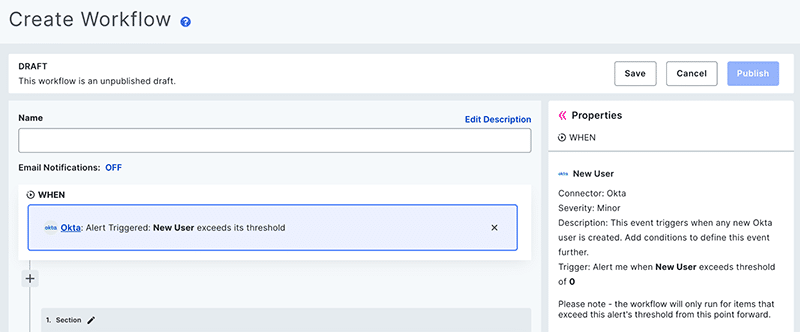
Alert on new Okta user creation
With attacks like these, adversaries who’ve compromised Okta’s systems will sometimes create a new user using customer’s stolen credentials. These users allow the attacker to gain access to customer’s critical systems for a period of time longer than the stolen session tokens. IT can stay on top of things by paying attention to whenever a new Okta user is created.
To create an alert, build a new workflow triggered on the Okta New User event.
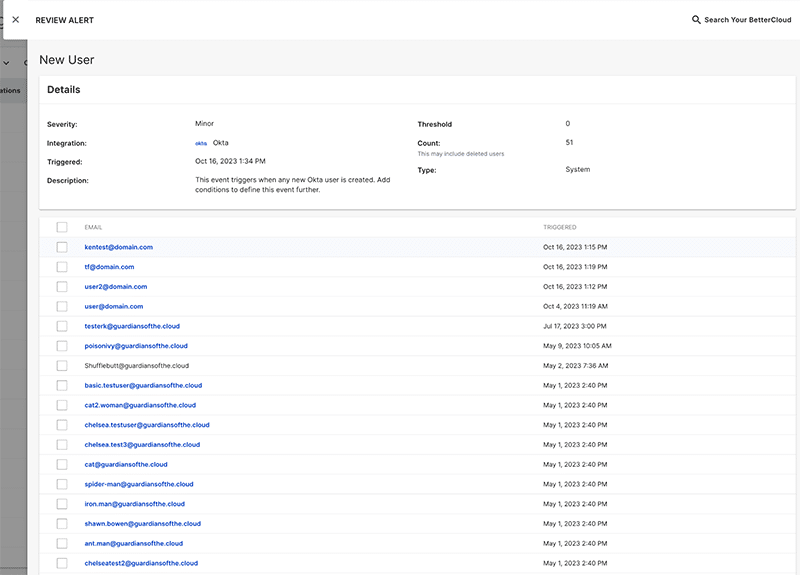
Once deployed, a new Alert will appear in the Alerts tab with a list of Okta users which have triggered the alert. We recommend IT teams periodically review this report for any suspicious activity.
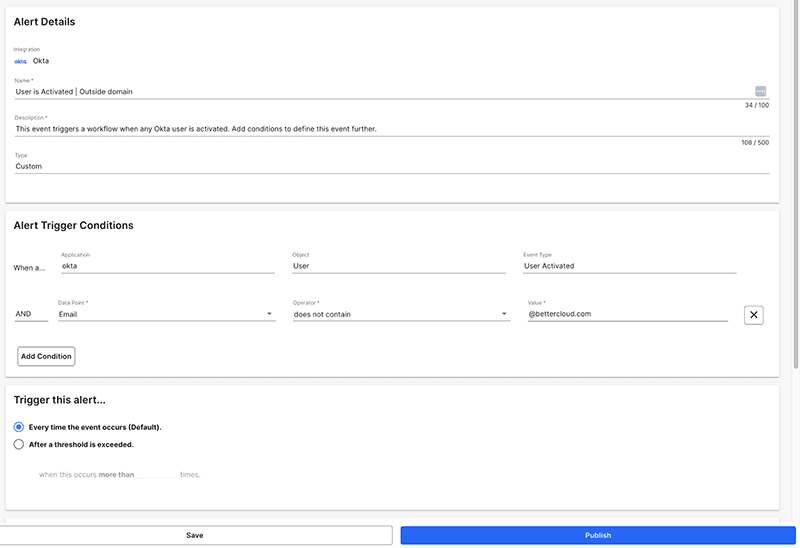
Alert on Okta user reactivation
While BetterCloud doesn’t detect reactivations in Okta today, we can alert IT of Okta users who’ve just been activated. Essentially this means a user has joined the Okta domain, which may indicate an attacker has joined your organization using credentials stolen from an Okta breach.
BetterCloud users can create an alert to detect this activity by building a workflow which triggers on the Okta User Activated event. Once deployed, the alert will appear in the alerts page where it can be further configured.
Conclusion
With IT being more overworked than ever, it’s essential IT leaders deliberately choose products and vendors committed to making their teams work smarter. BetterCloud has been leading the charge for over a decade since starting the SaaSOps revolution. While we’re sad to see so many companies impacted by this series of Okta breaches, we’re committed to helping our customers ensure business continuity through automated monitoring.
If you’d like to learn more, reach out to learn more about how to use BetterCloud to secure your Okta environment. Or join the discussion about this blog post on our BetterIT Slack community. Our team is here, eager and ready to answer any questions you might have!
[ad_2]
Source link
